Recently, we discovered a security issue with the way IT-Boost handles TOTP Secrets. IT-Boost has the feature to calculate OTP codes, ideal for sharing credentials within a team. When a user does not have access to IT-Boost anymore, they also lose access to the credentials and TOTP Generator. We discovered […]
We've developed a C# Function App designed to balance devices from a main group into various Wave groups. This app can run on a recurring schedule, rebalancing devices as needed when there are changes in the number of devices due to growth or shrinkage.
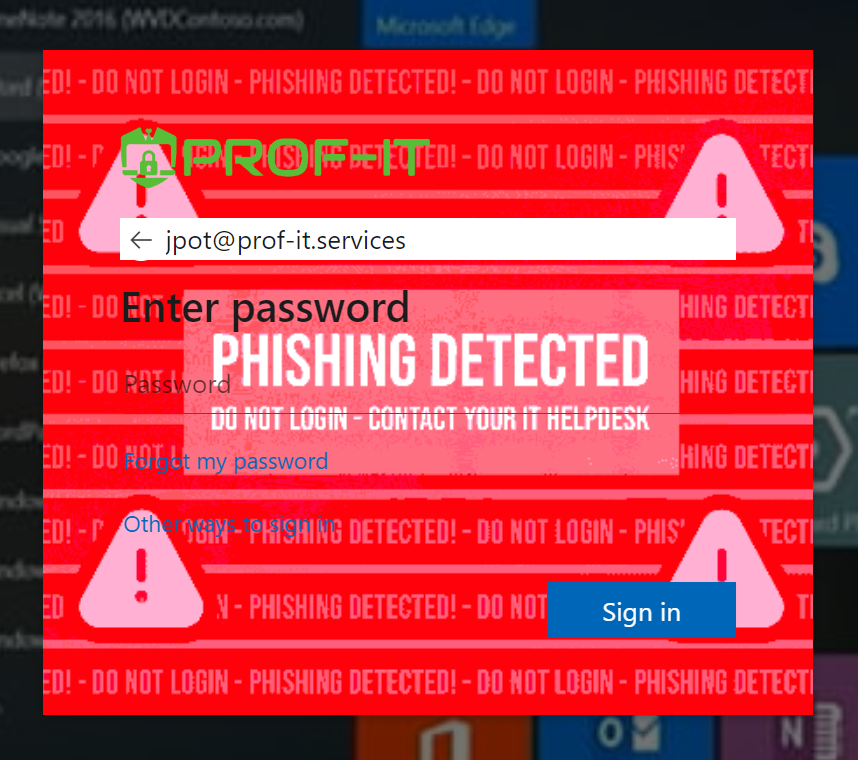
Exciting news! 🎉 We’re enhancing our Microsoft 365 security with advanced agentless CSS phishing detection. For free, for everyone. Using custom CSS and a server-side solution, we can swiftly detect phishing attacks and receive automatic alerts upon detection. During each login, our servers validate the login session, and users are […]
I’ve recently encountered an issue where malicious email was imported into the Zendesk platform, while it was successfully quarantined by Microsoft 365. In this post, I go over the options to mitigate this threat. The problem lies in the fact that forwarding takes place prior to the email being processed […]
This improved Sentinel Analytics Rule can be used to detect malicious Inbox Rules used by threat actors to hide invoice fraud activity. I've used the Inbox rule currently available as a template within Sentinel, and modified it to alert on Outlook rules I encountered in the wild.
A checklist to follow for Microsoft 365 accounts that are compromised
How do you ensure each endpoint is properly synced and redirected? What if important data is lost due to a misconfiguration? Run this script from RMM or Intune Proactive Remediations in the user context. Exit 1 and output are generated when issues occur. Do you need help with your Modern […]
Microsoft 365 is often considered safe, as it's always up to date and maintained by Microsoft.
Unfortunately, this is not true! Well, at least some parts aren't. There are quite some options and products/features that should be configured to limit risk and exposure.
In this post, I’m outlining the most important security settings and products, everyone should implement.
Use this PowerShell script and Azure logic app to get the Entra ID Group membership of a user in a safe and secure way. I’ve created this solution to be able to execute certain code based on the user’s group membership. Back in the day it would be easy to […]
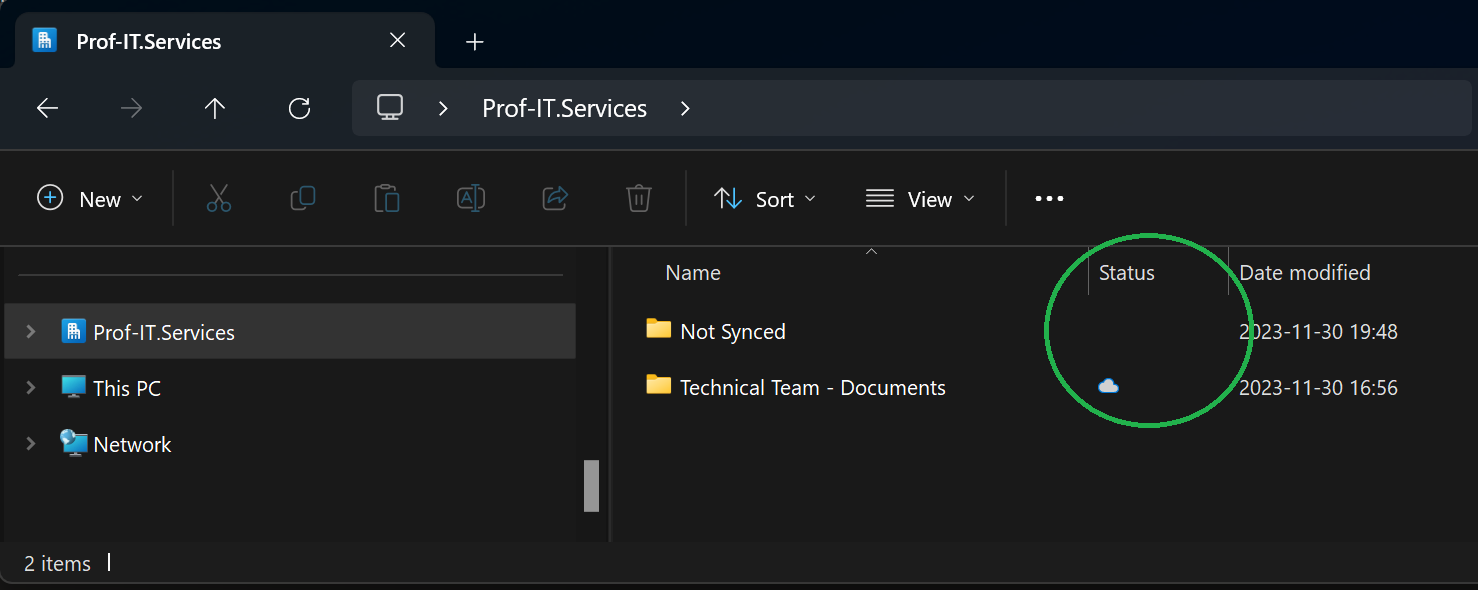
What happens with data that exists only locally on a Device? When users manually create a folder on their device, within the root directory of the SharePoint OneDrive Folder, it exists only locally, it’s un-synced and lacks the cloud functionality and benefits of SharePoint including file versioning and backups. I […]
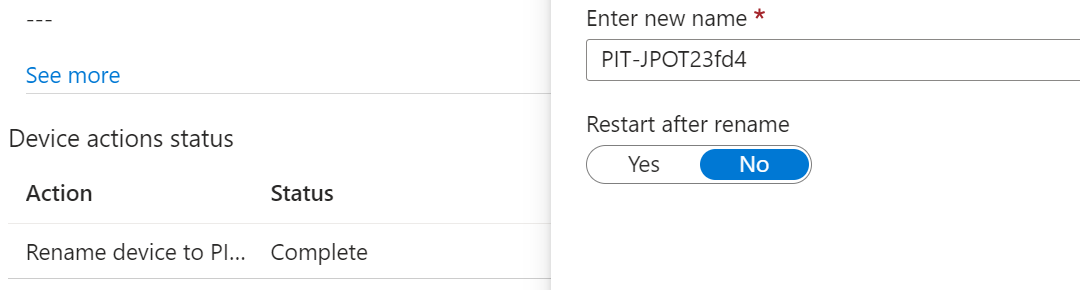
Follow the steps in this blog to seamlessly rename your Intune devices, appending the primary assigned user’s UPN along with a random suffix. I’ve created this Logic App that renames the devices as the Intune options are limited to the serial number and random generated values. Both are not easy […]
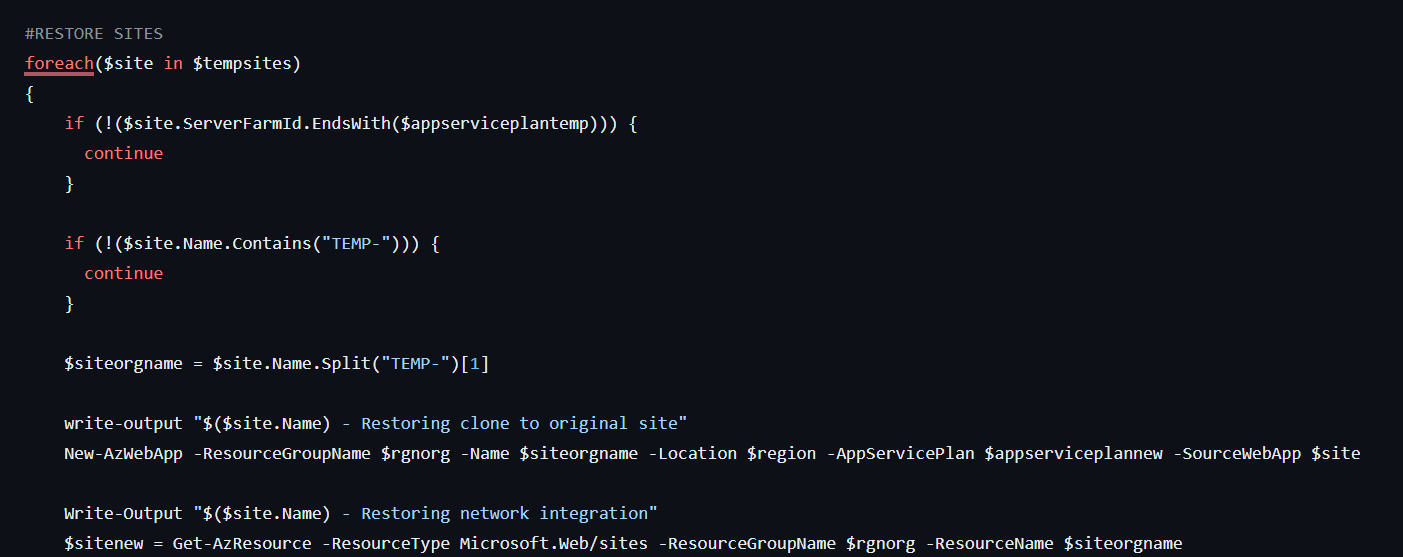
Microsoft has released a new Azure Mv3 series App Service Plan, which has double the amount of ram. In this blog I explain how to deploy and migrate your existing web apps. The M series are hosted on different servers, you won’t be able to upgrade or scale to this […]
To make life a bit easier, I’ve written this C# .NET Core Console application to sync the asset device names to the Asset Tag so it is visible in the HaloPSA portal. The application loops through all the devices separately, so you might want to run it not too often […]
Azure File Shares do not behave the same as a SMB share hosted on a Windows Server and there are challenges when you connect from non-domain joined computers. In this blog I’ll go over the lessons I learned implementing them. Feel free to shoot me a message on LinkedIn if […]
Use this PowerShell script and Azure logic app to sync library’s based on Azure AD Group assignments. Ever had to Sync 100 folders to 10 or more different security groups, and didn’t want to create configuration profiles for each group? Or had to wait up to 8 hours before Intune […]
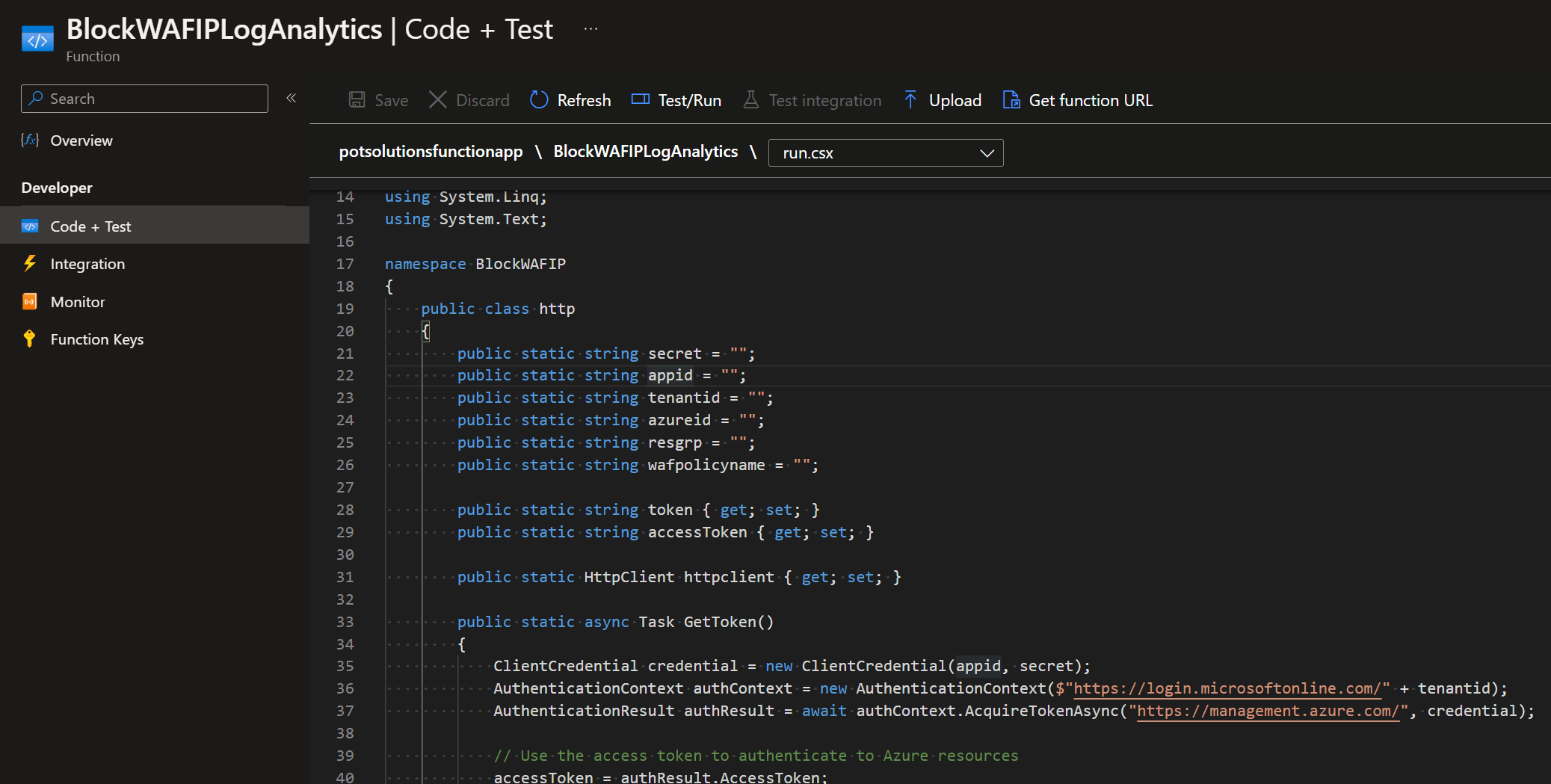
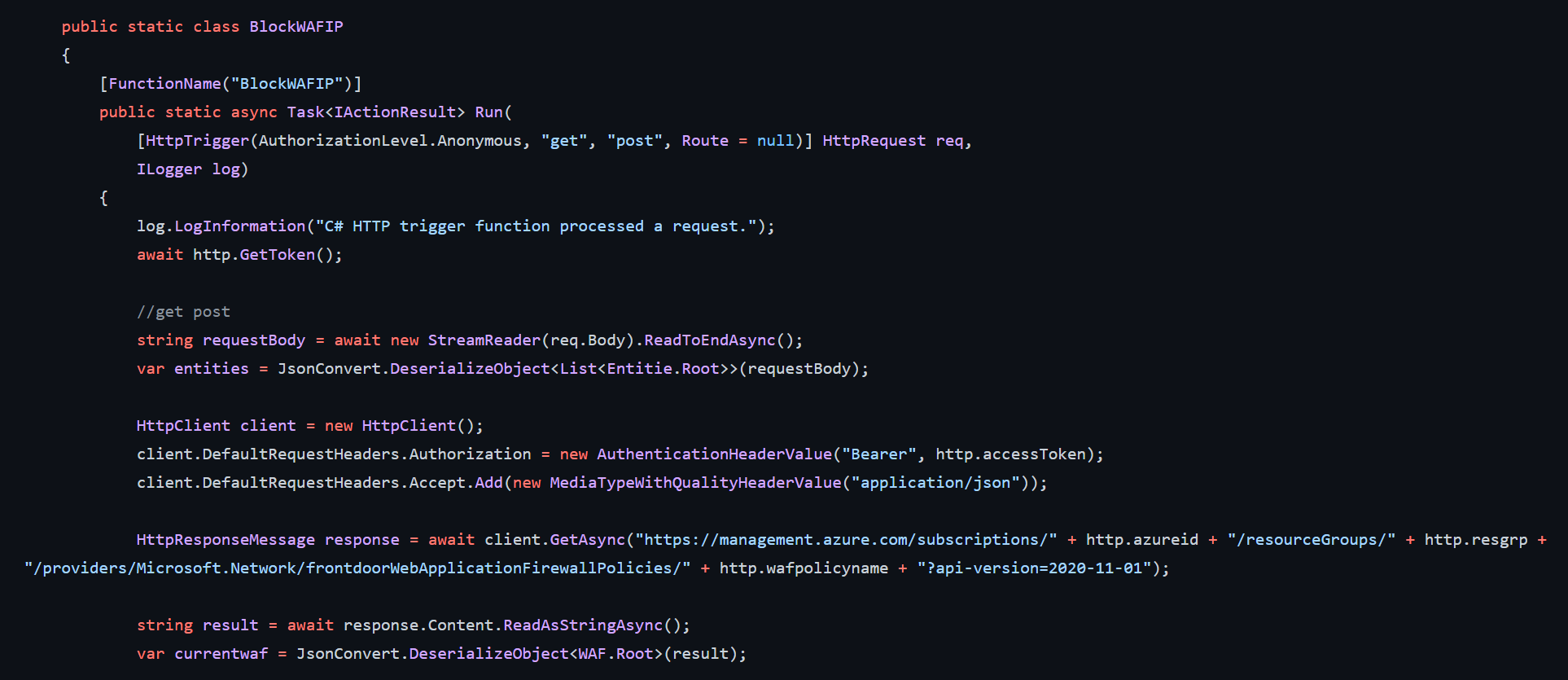
Use this function and logic app, to block abusive IP addresses using a custom rule, that hit a certain block limit on Azure WAF / Frontdoor. Leveraging Log Analytics Alerts. This greatly improves security for your origins, as threat actors won’t be able to scan indefinitely (or until rate limit […]
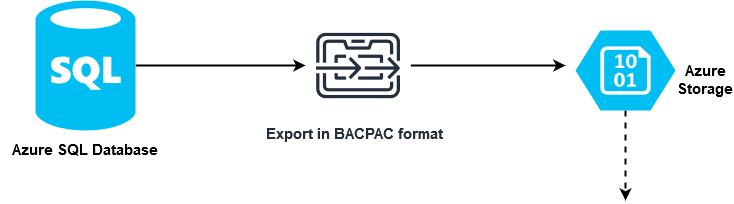
Use these instructions to automate SQL backup to a storage account with private endpoints. WHY Azure SQL Services work great, have high availability options, built-in backup functionality, but what if someone breaks into your Azure Tenants and deletes everything!? There are (expensive) SQL backup solutions that use various CPU-intensive techniques […]
Please read blog 2, using Log Analytics is more cost effective and doesn’t have a 10 entity limit. https://potsolutions.nl/2023/05/20/block-sentinel-log-analytics-entities-on-azure-waf-2/ Azure Frontdoor is a powerful tool for managing web traffic, but it doesn’t always provide enough protection against malicious incoming requests. In particular, it doesn’t have a built-in feature for blocking […]
2578 Broadway #579
New York 10025
United States
Korte Lijnbaanssteeg 1-4261
1012SL, Amsterdam
The Netherlands