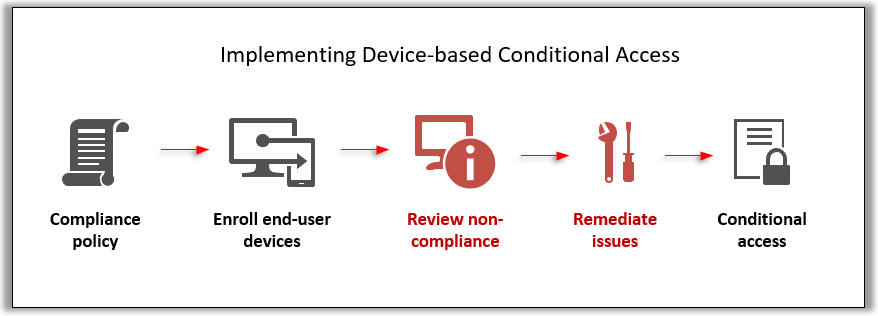
All devices should be compliance before company resources can be accessed. The compliance policies include the following:
- Device Encryption
- Windows Firewall status
- Defender For Endpoint status & threat level
- Minimum versions for iOS, Android, and Windows
- Windows TPM & Secure Boot
Compliance status for all devices can be verified on Devices – Microsoft Intune admin center
Click on the device you want to verify, Device compliance.
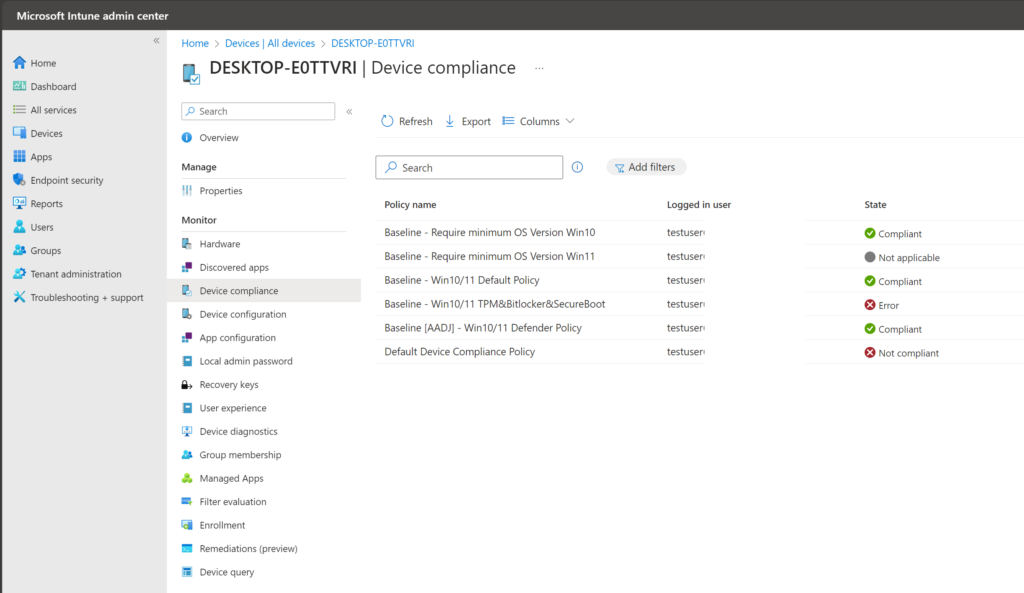
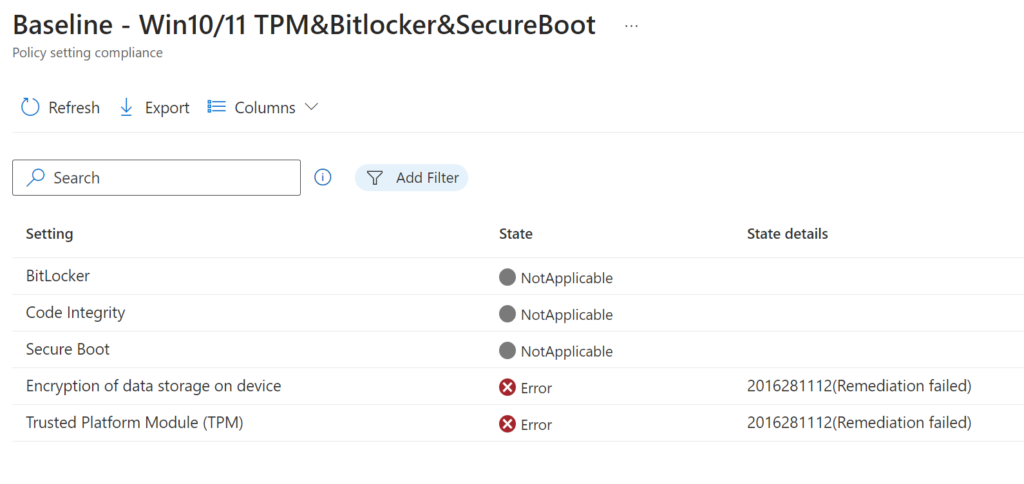
Common issues
Defender for Endpoint status can be an issue if there is a third-part AV installed. Uninstall all that you can find.
Defender for Endpoint threat level – compliance issues regarding this should be taken verry seriously as it could indicate there is a threat on the device. Review incidents alerts, and the device on Security & Compliance (microsoft.com)
BitLocker will be auto enabled, recovery keys will be saved in Entra ID. Policies do require a certain device encryption cryptography. Should there be any conflicts, it’s often enough to decrypt the drive, and enable encryption again.
Secure Boot should always be enabled. Follow these instructions to enable in case it isn’t. It does often require entering the Bios settings, facetiming with the user could be usefull.
Windows 11 and Secure Boot – Microsoft Support
TPM needs to be enabled as well. It also requires access to Bios if it isn’t enabled. There is also TPM.MSC that can be used to configure and verify status.
Enable TPM 2.0 on your PC – Microsoft Support