Leverage our white-labeled Modern Workplace Services to improve the environment of your clients.
Prof-IT’s standardized Managed M365 Intune environment suits every business, and is scoped to mobile, physical devices and virtual environments such as AVD or W365.
Several platform features can be enabled/disabled per tenant, such as:
- Auto-disable Entra ID shared mailbox accounts to decrease attack surface
- Auto rename devices to CODE+UPN+RAND
- Auto Assign devices to most frequently signed-in user
- M365 CSS Phishing Protection
- Several user notifications
Our service includes:
- Intune management
- Vulnerability Management
- Third-Party Patching
- Device Monitoring
- Microsoft Sentinel
- Security Orchestration
- and much more!
View more details below, on our knowledgebase, request our white paper, or contact us for a meeting!
White-labeled Solutions
Brand them as your own and deliver seamless experiences to your customers. Our vulnerability and desktop notifications can be branded with your logo and details.
Vulnerability Management
Stay ahead of threats with comprehensive security measures. We ensure proper settings are in place, and update third-party applications where possible.
Compliance Excellence
Our services adhere to all major security frameworks, ensuring peace of mind for you and your clients. We continuously improve the platform and update managed customers.
one vendor without dependencies
No third-party solutions or infrastructure is required other than our managed service. We ensure proper functionality, security and compliance.
SECURITY BEST PRACTICES
All known and lesser-known security best practices are included in our baseline, remediating a wide range of security risks.
Some examples:
- Customized Exchange rules that block known malicious email patterns
- Exchange NDR turned off
- Phish and Spam protection policies
- Entra ID risk remediation
- Guest access limitations
- PowerAutomate Tenant Isolation
SECURITY ORCHESTRATION, AUTOMATION, AND RESPONSE (SOAR)
Advanced monitoring and response capabilities scan for malicious activities, and our custom automation engine isolates users and devices during high-severity incidents.
This containment ensures that potential security threats are neutralized, safeguarding data, systems, and the integrity of the environment.
Our automation engine takes action in your environment 24×7 for malicious activity and alerts.
Device Monitoring based on Azure Monitor
Multi-Tenant Device Monitoring
Our monitoring and remediation solution utilizes our in-house developed monitoring app, and Azure Monitoring to keep track of vital device health, such as OneDrive and SharePoint health, Defender for Endpoint Health, and more.
This solution doesn’t require any RMM agent, nor does it have any dependencies on Intune Remediations and E3 or E5 licenses.
A Log Analytics workspace is deployed in each customer’s tenant, ensuring data remains in each client’s environment, and is billed based on their own ingested data. This makes it extremely suitable for highly regulated environments.
Zero-Trust Management
Leveraging our platform, we manage, monitor and proactively remediate issues in every tenant we manage.
Microsoft 365 management
Leveraging products like Intune and Entra, enriched with our in-house developed applications, we ensure all accounts, virtual, mobile and physical devices are in crisp shape, fully secure and compliant!
This ensures that high-risk, unmanaged computers are prevented from accessing the environment, resulting in a safe and phish-resistant environment.
Application & Vulnerability management
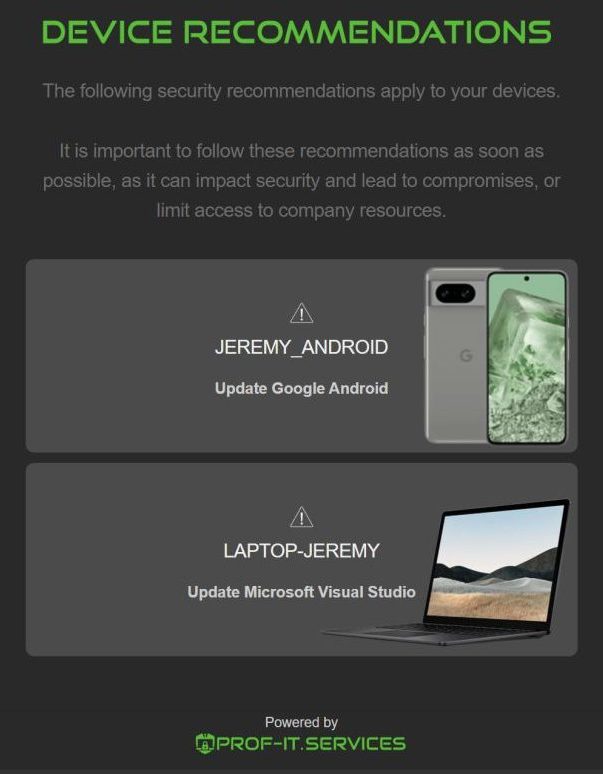
Up-to-date devices and applications are important to prevent breaches, and also increase user experience. Leveraging our in-house developed remediation tool, we ensure that third-party applications are up to date.
We notify users by email and desktop notifications when manual actions are needed, for example for unmanaged Android devices requiring updates.
Microsoft 365 phishing protection & SOAR
Our advanced phishing detection works on any device, for all users, and protects against modern Man In The Middle phishing attacks, which regular MFA does not protect against.
Phish Detections flow through our Managed Microsoft Sentinel SOC, which generates alerts that include the user’s IP address and phish URL.
When a positive phishing attack is confirmed, our SOAR platform automatically blocks the URL on all managed tenants, and reports the URL to Microsoft.
Application Packaging & Deployment
Multiple methods exist for packaging and deploying applications. Leveraging these methods ensures an auto-enrollment experience for new devices and users, resulting in less manual labor.
1. Chocolatey
• Uses a community repository to download and install applications.
• Many applications such as browsers are easily installable.
• Can easily be scripted and deployed from Intune.
• Does not require expertise.
• Requires private hosting solution.
The regular Chocolatey community version is not well-suitable for companies due to rate-limiting. Prof-IT Services hosts a private Chocolatey repository with malware scans, that does not have this limitation. This service is included in the managed service.
2. MSIX Application Packaging
• Applications are recorded and deployed in a virtual bubble.
• Can easily be installed, uninstalled, and updated.
• Requires expertise.
MSIX application packaging is a simplified way to create and deploy legacy applications. Applications can be packaged into the MSIX format and distributed to managed Windows devices via Intune. This process ensures smooth installation and updates, making app management easier and more reliable.
3. PowerShell & Intune Package
• Used if other options are not available, or if more flexibility is required.
• Requires expertise.
Most normal user/client applications that are deployed from Intune, can be packaged in MSIX format or are available on Chocolatey, others can be scripted with PowerShell.
Prof-IT Services has a dedicated packaging team available that specializes in application packaging.
Request our white paper!
Our managed modern workplace services and platform automation features are not limited to those listed on this webpage. Request our service description white-paper to learn more.
Do you have specific platform requests or requirements? Contact us and we’ll consider it for our roadmap.
2578 Broadway #579
New York 10025
United States
Paxlaan 10 #9129
2131 PZ, Hoofddorp
The Netherlands
