It’s time to secure Google Workspace—even if you’re not using it. Read about our recent discovered vulnerability, called 'G-Door', which allows users to bypass Microsoft 365 conditional access rules.
Recently, we encountered two distinct variants of a payload delivered through Google Drive, both containing a […]
How to Guard Against Token Theft for Microsoft 365 Session hijacking occurs when an attacker steals […]
Recently, we discovered a security issue with how IT-Boost handles TOTP secrets. IT-Boost can calculate OTP […]
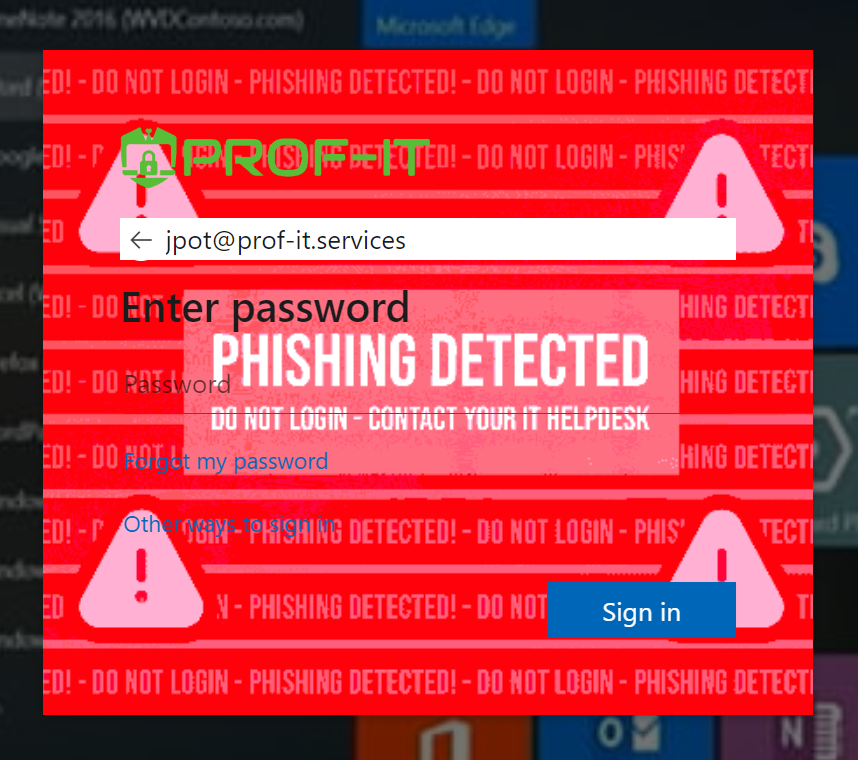
Exciting news! 🎉 We’ve recently created this advanced CSS phishing protection, and we’re making it available […]
I’ve recently encountered an issue where malicious email was imported into the Zendesk platform, while it […]
This improved Sentinel Analytics Rule can be used to detect malicious Inbox Rules used by threat actors to hide invoice fraud activity. I've used the Inbox rule currently available as a template within Sentinel, and modified it to alert on Outlook rules I encountered in the wild.
A checklist to follow for Microsoft 365 accounts that are compromised
Microsoft 365 is often considered safe, as it's always up to date and maintained by Microsoft.
Unfortunately, this is not true! Well, at least some parts aren't. There are quite some options and products/features that should be configured to limit risk and exposure.
In this post, I’m outlining the most important security settings and products, everyone should implement.