It’s time to secure Google Workspace—even if you’re not using it. Read about our recent discovered vulnerability, called 'G-Door', which allows users to bypass Microsoft 365 conditional access rules.
Recently, we encountered two distinct variants of a payload delivered through Google Drive, both containing a […]
Managing a SharePoint environment can be a complex task, especially when it comes to ensuring that […]
How to Guard Against Token Theft for Microsoft 365 Session hijacking occurs when an attacker steals […]
We've developed a C# Function App designed to balance devices from a main group into various Wave groups. This app can run on a recurring schedule, rebalancing devices as needed when there are changes in the number of devices due to growth or shrinkage.
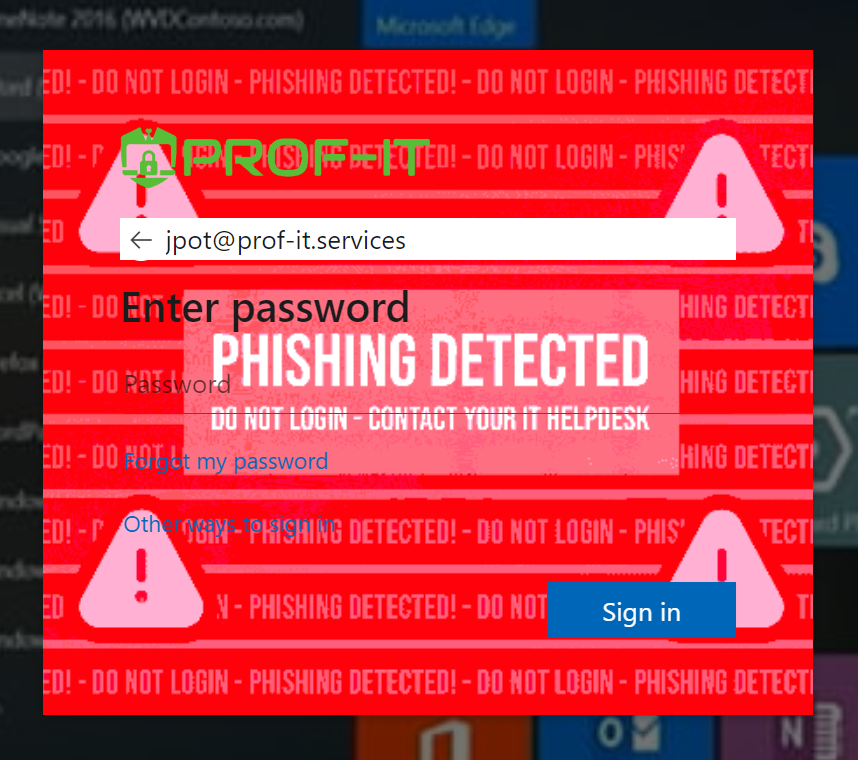
Exciting news! 🎉 We’ve recently created this advanced CSS phishing protection, and we’re making it available […]
I’ve recently encountered an issue where malicious email was imported into the Zendesk platform, while it […]